cypherpunks
4d ago
•
100%
cypherpunks
4d ago
•
100%
is your proposal inspired by Biden administration forgives $4.5 billion in student debt for over 60,000 public service workers ?
 cypherpunks
4d ago
•
100%
cypherpunks
4d ago
•
100%
The headline should mention that they're breaking 22-bit RSA, but then it would get a lot less clicks.
A different group of Chinese researchers set what I think is the current record when they factored a 48-bit number with a quantum computer two years ago: https://arxiv.org/abs/2212.12372
I guess the news here is that now they've reached 22 bits using the quantum annealing technique which works on D-Wave's commercially-available quantum computers? That approach was previously able to factor an 18-bit number in 2018.
🥂 to the researchers, but 👎 to the clickbait headline writers. This is still nowhere near being a CRQC (cryptanalytically-relevant quantum computer).
 www.theregister.com
www.theregister.com
cross-posted from: https://lemmy.ml/post/21476364 > from *The Register*: > > A Chinese industry group has accused Intel of backdooring its CPUs, in addition to other questionable security practices while calling for an investigation into the chipmaker, claiming its products pose "serious risks to national security." > > > >The Cybersecurity Association of China (CSAC), in a lengthy [post](https://mp.weixin.qq.com/s/rgRmOfoPr7x1TZhyb-1ifg) on its WeChat account on Wednesday described Intel's chips as being riddled with vulnerabilities, adding that the American company's "major defects in product quality and security management show its extremely irresponsible attitude towards customers." > > > >The CSAC also accused Intel of embedding a backdoor "in almost all" of its CPUs since 2008 as part of a "next-generation security defense system" developed by the US National Security Agency. > > > >This allowed Uncle Sam to "build an ideal monitoring environment where only the NSA is protected and everyone else is 'naked,'" the post continued. "This poses a huge security threat to the critical information infrastructure of countries around the world, including China," the industry group claims. > > > >The infosec org also recommends the Cyberspace Administration of China open an investigation into the security of Intel's products sold in the country "to effectively safeguard China's national security and the legitimate rights and interests of Chinese consumers." > > > >Intel did not immediately respond to The Register's inquiries. > > --- > Here is a machine translation (via google translate) of [CSAC's post](https://mp.weixin.qq.com/s/rgRmOfoPr7x1TZhyb-1ifg): > > >Frequent vulnerabilities and high failure rates. Intel product cybersecurity risks should be systematically checked > > > >China Cyberspace Security Association October 16, 2024 09:02 > > > >Frequent vulnerabilities and high failure rates > > > >Intel product cybersecurity risks should be systematically checked > > > >1. Frequent security vulnerabilities > > > >In August 2023, Intel CPU was exposed to the Downfall vulnerability, which is a CPU transient execution side channel vulnerability. It uses the Gather instruction in its AVX2 or AVX-512 instruction set to obtain sensitive data such as keys, user information, and key parameters previously stored in a specific vector register buffer. The vulnerability affects Intel's 6th to 11th generation Core, Celeron, and Pentium series CPUs, as well as 1st to 4th generation Xeon processors. In fact, as early as 2022, researchers reported the vulnerability to Intel, but Intel, knowing the existence of the vulnerability, neither acknowledged it nor took effective action. It continued to sell products with vulnerabilities until the vulnerability was publicly reported, and Intel was forced to take vulnerability repair measures. Five victims have filed a class action lawsuit against Intel in November 2023 in the San Jose Branch of the U.S. Federal District Court for the Northern California in the name of themselves and representatives of "CPU consumers across the United States". > > > >Coincidentally, in November 2023, Google researchers disclosed that Intel CPUs have a high-risk vulnerability, Reptar. Exploiting this vulnerability, attackers can not only obtain sensitive data such as personal accounts, card numbers and passwords in the system in a multi-tenant virtualization environment, but also cause the physical system to hang or crash, resulting in denial of service for other systems and tenants it carries. > > > >Since 2024, Intel CPUs have successively exposed vulnerabilities such as GhostRace, NativeBHI, and Indirector. Intel's major defects in product quality and security management show its extremely irresponsible attitude towards customers. > > > >2. Poor reliability and indifference to user complaints > > > >Since the end of 2023, a large number of users have reported that crashes occur when using Intel's 13th and 14th generation Core i9 series CPUs to play specific games. Game manufacturers have even added pop-up processing in the game to warn users who use these CPUs. Dylan Browne, Unreal Engine Supervisor and Visual Effects Manager at visual effects studio ModelFarm, posted that the failure rate of computers using Intel processors in his company was as high as 50%. > > > >With concentrated user feedback and no way to cover up, Intel finally had to admit that there were stability issues with its products and issued a so-called preliminary investigation report, attributing the problem to the motherboard manufacturer setting too high a voltage. However, it was immediately refuted by the motherboard manufacturer, who stated that the motherboards it produced were developed according to the data provided by Intel for BIOS programs, and the cause of the crash was not the motherboard manufacturer. In July 2024, Intel issued a statement to explain the frequent CPU crashes, admitting that due to the incorrect microcode algorithm sending too high a voltage request to the processor, some 13th and 14th generation processors became unstable. > > > >Frequent crashes occurred at the end of 2023, and Intel only identified the problem and provided an update program half a year later, and the mitigation measures given within half a year did not work, which fully reflected that Intel did not actively and honestly face the problems when facing its own product defects, but simply ignored, shirked and procrastinated. Some professionals speculate that the root cause is that Intel has actively sacrificed product stability in order to gain performance improvements and regain competitive advantages. It is also reported that the US law firm "Abington Cole + Ellery" has begun investigating the instability of Intel's 13th and 14th generation processors, and will file a class action lawsuit on behalf of end users. > > > >3. Under the guise of remote management, the real purpose is to monitor users > > > >Intel, together with HP and other manufacturers, jointly designed the IPMI (Intelligent Platform Management Interface) technical specification, claiming that it is to monitor the physical health characteristics of the server, and technically manages and controls the server through the BMC (Baseboard Management Controller) module. The BMC module allows users to remotely manage devices, and can realize functions such as starting the computer, reinstalling the operating system, and mounting ISO images. The module has also been exposed to high-risk vulnerabilities (such as CVE-2019-11181), resulting in a large number of servers around the world facing great security risks of being attacked and controlled. > > > >In addition, Intel also integrates third-party open source components with serious vulnerabilities in its products. Taking the Intel M10JNPSB server motherboard as an example, this product supports IPMI management and is currently out of after-sales service. The last firmware update package was released on December 13, 2022. Analysis shows that its web server is lighttpd, with version number 1.4.35, which is actually the version of March 12, 2014. At that time, the latest version of lighttpd had been upgraded to 1.4.66. The difference between the two is 9 years, which is surprisingly large. This irresponsible behavior puts the network and data security of the majority of server users at great risk. > > > >4. Hidden backdoors endanger network and information security > > > >The autonomous running subsystem ME (Management Engine) developed by Intel has been embedded in almost all Intel CPUs since 2008. It is part of its vigorously promoted AMT (Active Management Technology), allowing system administrators to perform tasks remotely. As long as this function is activated, the computer can be accessed remotely regardless of whether the operating system is installed. Based on the redirection technology of peripherals such as optical drives, floppy drives, and USB, it can achieve the effect of physical contact with the user's computer. Hardware security expert Damien Zammit pointed out that ME is a backdoor that can fully access the memory, bypass the operating system firewall, send and receive network packets without the operating system user's knowledge, and users cannot disable ME. Intel AMT (Active Management Technology) based on ME technology was exposed to have a high-risk vulnerability (CVE-2017-5689) in 2017. Attackers can bypass the authentication mechanism and log in to the system directly to obtain the highest authority by setting the response field in the login parameters to empty. > > > >In August 2017, Russian security experts Mark Ermolov and Maxim Goryachy found a hidden switch suspected to be set by the NSA (National Security Agency) through reverse engineering technology. The switch is located in the HAP bit in the PCHSTERP0 field, but the flag bit is not recorded in the official document. Dramatically, HAP is the full name of High Assurance Platform, which belongs to the NSA-initiated project to build a next-generation security defense system. > > > >If the NSA directly shuts down the ME system by turning on the hidden switch of the HAP bit, and at the same time all other Intel CPUs in the world run the ME system by default, it is equivalent to the NSA being able to build an ideal monitoring environment where only it is protected and everyone else is "naked". This poses a great security threat to the critical information infrastructure of countries around the world, including China. At present, the software and hardware on the ME are closed source, and its security mainly relies on Intel's unilateral commitment, but the facts show that Intel's commitment is pale and unconvincing. Using Intel products poses serious risks to national security. > > > >5. It is recommended to initiate a cybersecurity review > > > >According to reports, nearly a quarter of Intel's global annual revenue of more than US$50 billion comes from the Chinese market. In 2021, Intel's CPU accounted for about 77% of the domestic desktop market and about 81% of the notebook market; in 2022, Intel's x86 server market share in China was about 91%. It can be said that Intel has made a lot of money in China, but the company has continued to do things that harm China's interests and threaten China's national security. > > > >Previously, the US government passed the so-called "Chips and Science Act" to unreasonably exclude and suppress China's semiconductor industry. Intel is the biggest beneficiary of this bill. Intel CEO Pat Gelsinger successfully tied Intel to the US government and became the largest partner of the US chip strategy. It not only received $8.5 billion in direct subsidies, but also $11 billion in low-interest loans. > > > >In order to please the US government, Intel actively took a stand to suppress China on the so-called Xinjiang-related issues, requiring its suppliers not to use any labor, purchase products or services from the Xinjiang region. In its financial report, it even listed Taiwan Province on a par with China, the United States, and Singapore, and took the initiative to cut off supply and service to Chinese companies such as Huawei and ZTE. This is a typical "holding the bowl to eat, and putting down the bowl to smash the pot". > > > >It is recommended to initiate a cybersecurity review of Intel's products sold in China to effectively safeguard China's national security and the legitimate rights and interests of Chinese consumers. >
 www.theregister.com
www.theregister.com
cross-posted from: https://lemmy.ml/post/21476364 > from *The Register*: > > A Chinese industry group has accused Intel of backdooring its CPUs, in addition to other questionable security practices while calling for an investigation into the chipmaker, claiming its products pose "serious risks to national security." > > > >The Cybersecurity Association of China (CSAC), in a lengthy [post](https://mp.weixin.qq.com/s/rgRmOfoPr7x1TZhyb-1ifg) on its WeChat account on Wednesday described Intel's chips as being riddled with vulnerabilities, adding that the American company's "major defects in product quality and security management show its extremely irresponsible attitude towards customers." > > > >The CSAC also accused Intel of embedding a backdoor "in almost all" of its CPUs since 2008 as part of a "next-generation security defense system" developed by the US National Security Agency. > > > >This allowed Uncle Sam to "build an ideal monitoring environment where only the NSA is protected and everyone else is 'naked,'" the post continued. "This poses a huge security threat to the critical information infrastructure of countries around the world, including China," the industry group claims. > > > >The infosec org also recommends the Cyberspace Administration of China open an investigation into the security of Intel's products sold in the country "to effectively safeguard China's national security and the legitimate rights and interests of Chinese consumers." > > > >Intel did not immediately respond to The Register's inquiries. > > --- > Here is a machine translation (via google translate) of [CSAC's post](https://mp.weixin.qq.com/s/rgRmOfoPr7x1TZhyb-1ifg): > > >Frequent vulnerabilities and high failure rates. Intel product cybersecurity risks should be systematically checked > > > >China Cyberspace Security Association October 16, 2024 09:02 > > > >Frequent vulnerabilities and high failure rates > > > >Intel product cybersecurity risks should be systematically checked > > > >1. Frequent security vulnerabilities > > > >In August 2023, Intel CPU was exposed to the Downfall vulnerability, which is a CPU transient execution side channel vulnerability. It uses the Gather instruction in its AVX2 or AVX-512 instruction set to obtain sensitive data such as keys, user information, and key parameters previously stored in a specific vector register buffer. The vulnerability affects Intel's 6th to 11th generation Core, Celeron, and Pentium series CPUs, as well as 1st to 4th generation Xeon processors. In fact, as early as 2022, researchers reported the vulnerability to Intel, but Intel, knowing the existence of the vulnerability, neither acknowledged it nor took effective action. It continued to sell products with vulnerabilities until the vulnerability was publicly reported, and Intel was forced to take vulnerability repair measures. Five victims have filed a class action lawsuit against Intel in November 2023 in the San Jose Branch of the U.S. Federal District Court for the Northern California in the name of themselves and representatives of "CPU consumers across the United States". > > > >Coincidentally, in November 2023, Google researchers disclosed that Intel CPUs have a high-risk vulnerability, Reptar. Exploiting this vulnerability, attackers can not only obtain sensitive data such as personal accounts, card numbers and passwords in the system in a multi-tenant virtualization environment, but also cause the physical system to hang or crash, resulting in denial of service for other systems and tenants it carries. > > > >Since 2024, Intel CPUs have successively exposed vulnerabilities such as GhostRace, NativeBHI, and Indirector. Intel's major defects in product quality and security management show its extremely irresponsible attitude towards customers. > > > >2. Poor reliability and indifference to user complaints > > > >Since the end of 2023, a large number of users have reported that crashes occur when using Intel's 13th and 14th generation Core i9 series CPUs to play specific games. Game manufacturers have even added pop-up processing in the game to warn users who use these CPUs. Dylan Browne, Unreal Engine Supervisor and Visual Effects Manager at visual effects studio ModelFarm, posted that the failure rate of computers using Intel processors in his company was as high as 50%. > > > >With concentrated user feedback and no way to cover up, Intel finally had to admit that there were stability issues with its products and issued a so-called preliminary investigation report, attributing the problem to the motherboard manufacturer setting too high a voltage. However, it was immediately refuted by the motherboard manufacturer, who stated that the motherboards it produced were developed according to the data provided by Intel for BIOS programs, and the cause of the crash was not the motherboard manufacturer. In July 2024, Intel issued a statement to explain the frequent CPU crashes, admitting that due to the incorrect microcode algorithm sending too high a voltage request to the processor, some 13th and 14th generation processors became unstable. > > > >Frequent crashes occurred at the end of 2023, and Intel only identified the problem and provided an update program half a year later, and the mitigation measures given within half a year did not work, which fully reflected that Intel did not actively and honestly face the problems when facing its own product defects, but simply ignored, shirked and procrastinated. Some professionals speculate that the root cause is that Intel has actively sacrificed product stability in order to gain performance improvements and regain competitive advantages. It is also reported that the US law firm "Abington Cole + Ellery" has begun investigating the instability of Intel's 13th and 14th generation processors, and will file a class action lawsuit on behalf of end users. > > > >3. Under the guise of remote management, the real purpose is to monitor users > > > >Intel, together with HP and other manufacturers, jointly designed the IPMI (Intelligent Platform Management Interface) technical specification, claiming that it is to monitor the physical health characteristics of the server, and technically manages and controls the server through the BMC (Baseboard Management Controller) module. The BMC module allows users to remotely manage devices, and can realize functions such as starting the computer, reinstalling the operating system, and mounting ISO images. The module has also been exposed to high-risk vulnerabilities (such as CVE-2019-11181), resulting in a large number of servers around the world facing great security risks of being attacked and controlled. > > > >In addition, Intel also integrates third-party open source components with serious vulnerabilities in its products. Taking the Intel M10JNPSB server motherboard as an example, this product supports IPMI management and is currently out of after-sales service. The last firmware update package was released on December 13, 2022. Analysis shows that its web server is lighttpd, with version number 1.4.35, which is actually the version of March 12, 2014. At that time, the latest version of lighttpd had been upgraded to 1.4.66. The difference between the two is 9 years, which is surprisingly large. This irresponsible behavior puts the network and data security of the majority of server users at great risk. > > > >4. Hidden backdoors endanger network and information security > > > >The autonomous running subsystem ME (Management Engine) developed by Intel has been embedded in almost all Intel CPUs since 2008. It is part of its vigorously promoted AMT (Active Management Technology), allowing system administrators to perform tasks remotely. As long as this function is activated, the computer can be accessed remotely regardless of whether the operating system is installed. Based on the redirection technology of peripherals such as optical drives, floppy drives, and USB, it can achieve the effect of physical contact with the user's computer. Hardware security expert Damien Zammit pointed out that ME is a backdoor that can fully access the memory, bypass the operating system firewall, send and receive network packets without the operating system user's knowledge, and users cannot disable ME. Intel AMT (Active Management Technology) based on ME technology was exposed to have a high-risk vulnerability (CVE-2017-5689) in 2017. Attackers can bypass the authentication mechanism and log in to the system directly to obtain the highest authority by setting the response field in the login parameters to empty. > > > >In August 2017, Russian security experts Mark Ermolov and Maxim Goryachy found a hidden switch suspected to be set by the NSA (National Security Agency) through reverse engineering technology. The switch is located in the HAP bit in the PCHSTERP0 field, but the flag bit is not recorded in the official document. Dramatically, HAP is the full name of High Assurance Platform, which belongs to the NSA-initiated project to build a next-generation security defense system. > > > >If the NSA directly shuts down the ME system by turning on the hidden switch of the HAP bit, and at the same time all other Intel CPUs in the world run the ME system by default, it is equivalent to the NSA being able to build an ideal monitoring environment where only it is protected and everyone else is "naked". This poses a great security threat to the critical information infrastructure of countries around the world, including China. At present, the software and hardware on the ME are closed source, and its security mainly relies on Intel's unilateral commitment, but the facts show that Intel's commitment is pale and unconvincing. Using Intel products poses serious risks to national security. > > > >5. It is recommended to initiate a cybersecurity review > > > >According to reports, nearly a quarter of Intel's global annual revenue of more than US$50 billion comes from the Chinese market. In 2021, Intel's CPU accounted for about 77% of the domestic desktop market and about 81% of the notebook market; in 2022, Intel's x86 server market share in China was about 91%. It can be said that Intel has made a lot of money in China, but the company has continued to do things that harm China's interests and threaten China's national security. > > > >Previously, the US government passed the so-called "Chips and Science Act" to unreasonably exclude and suppress China's semiconductor industry. Intel is the biggest beneficiary of this bill. Intel CEO Pat Gelsinger successfully tied Intel to the US government and became the largest partner of the US chip strategy. It not only received $8.5 billion in direct subsidies, but also $11 billion in low-interest loans. > > > >In order to please the US government, Intel actively took a stand to suppress China on the so-called Xinjiang-related issues, requiring its suppliers not to use any labor, purchase products or services from the Xinjiang region. In its financial report, it even listed Taiwan Province on a par with China, the United States, and Singapore, and took the initiative to cut off supply and service to Chinese companies such as Huawei and ZTE. This is a typical "holding the bowl to eat, and putting down the bowl to smash the pot". > > > >It is recommended to initiate a cybersecurity review of Intel's products sold in China to effectively safeguard China's national security and the legitimate rights and interests of Chinese consumers. >
 www.theregister.com
www.theregister.com
from *The Register*: > A Chinese industry group has accused Intel of backdooring its CPUs, in addition to other questionable security practices while calling for an investigation into the chipmaker, claiming its products pose "serious risks to national security." > >The Cybersecurity Association of China (CSAC), in a lengthy [post](https://mp.weixin.qq.com/s/rgRmOfoPr7x1TZhyb-1ifg) on its WeChat account on Wednesday described Intel's chips as being riddled with vulnerabilities, adding that the American company's "major defects in product quality and security management show its extremely irresponsible attitude towards customers." > >The CSAC also accused Intel of embedding a backdoor "in almost all" of its CPUs since 2008 as part of a "next-generation security defense system" developed by the US National Security Agency. > >This allowed Uncle Sam to "build an ideal monitoring environment where only the NSA is protected and everyone else is 'naked,'" the post continued. "This poses a huge security threat to the critical information infrastructure of countries around the world, including China," the industry group claims. > >The infosec org also recommends the Cyberspace Administration of China open an investigation into the security of Intel's products sold in the country "to effectively safeguard China's national security and the legitimate rights and interests of Chinese consumers." > >Intel did not immediately respond to The Register's inquiries. --- Here is a machine translation (via google translate) of [CSAC's post](https://mp.weixin.qq.com/s/rgRmOfoPr7x1TZhyb-1ifg): >Frequent vulnerabilities and high failure rates. Intel product cybersecurity risks should be systematically checked > >China Cyberspace Security Association October 16, 2024 09:02 > >Frequent vulnerabilities and high failure rates > >Intel product cybersecurity risks should be systematically checked > >1. Frequent security vulnerabilities > >In August 2023, Intel CPU was exposed to the Downfall vulnerability, which is a CPU transient execution side channel vulnerability. It uses the Gather instruction in its AVX2 or AVX-512 instruction set to obtain sensitive data such as keys, user information, and key parameters previously stored in a specific vector register buffer. The vulnerability affects Intel's 6th to 11th generation Core, Celeron, and Pentium series CPUs, as well as 1st to 4th generation Xeon processors. In fact, as early as 2022, researchers reported the vulnerability to Intel, but Intel, knowing the existence of the vulnerability, neither acknowledged it nor took effective action. It continued to sell products with vulnerabilities until the vulnerability was publicly reported, and Intel was forced to take vulnerability repair measures. Five victims have filed a class action lawsuit against Intel in November 2023 in the San Jose Branch of the U.S. Federal District Court for the Northern California in the name of themselves and representatives of "CPU consumers across the United States". > >Coincidentally, in November 2023, Google researchers disclosed that Intel CPUs have a high-risk vulnerability, Reptar. Exploiting this vulnerability, attackers can not only obtain sensitive data such as personal accounts, card numbers and passwords in the system in a multi-tenant virtualization environment, but also cause the physical system to hang or crash, resulting in denial of service for other systems and tenants it carries. > >Since 2024, Intel CPUs have successively exposed vulnerabilities such as GhostRace, NativeBHI, and Indirector. Intel's major defects in product quality and security management show its extremely irresponsible attitude towards customers. > >2. Poor reliability and indifference to user complaints > >Since the end of 2023, a large number of users have reported that crashes occur when using Intel's 13th and 14th generation Core i9 series CPUs to play specific games. Game manufacturers have even added pop-up processing in the game to warn users who use these CPUs. Dylan Browne, Unreal Engine Supervisor and Visual Effects Manager at visual effects studio ModelFarm, posted that the failure rate of computers using Intel processors in his company was as high as 50%. > >With concentrated user feedback and no way to cover up, Intel finally had to admit that there were stability issues with its products and issued a so-called preliminary investigation report, attributing the problem to the motherboard manufacturer setting too high a voltage. However, it was immediately refuted by the motherboard manufacturer, who stated that the motherboards it produced were developed according to the data provided by Intel for BIOS programs, and the cause of the crash was not the motherboard manufacturer. In July 2024, Intel issued a statement to explain the frequent CPU crashes, admitting that due to the incorrect microcode algorithm sending too high a voltage request to the processor, some 13th and 14th generation processors became unstable. > >Frequent crashes occurred at the end of 2023, and Intel only identified the problem and provided an update program half a year later, and the mitigation measures given within half a year did not work, which fully reflected that Intel did not actively and honestly face the problems when facing its own product defects, but simply ignored, shirked and procrastinated. Some professionals speculate that the root cause is that Intel has actively sacrificed product stability in order to gain performance improvements and regain competitive advantages. It is also reported that the US law firm "Abington Cole + Ellery" has begun investigating the instability of Intel's 13th and 14th generation processors, and will file a class action lawsuit on behalf of end users. > >3. Under the guise of remote management, the real purpose is to monitor users > >Intel, together with HP and other manufacturers, jointly designed the IPMI (Intelligent Platform Management Interface) technical specification, claiming that it is to monitor the physical health characteristics of the server, and technically manages and controls the server through the BMC (Baseboard Management Controller) module. The BMC module allows users to remotely manage devices, and can realize functions such as starting the computer, reinstalling the operating system, and mounting ISO images. The module has also been exposed to high-risk vulnerabilities (such as CVE-2019-11181), resulting in a large number of servers around the world facing great security risks of being attacked and controlled. > >In addition, Intel also integrates third-party open source components with serious vulnerabilities in its products. Taking the Intel M10JNPSB server motherboard as an example, this product supports IPMI management and is currently out of after-sales service. The last firmware update package was released on December 13, 2022. Analysis shows that its web server is lighttpd, with version number 1.4.35, which is actually the version of March 12, 2014. At that time, the latest version of lighttpd had been upgraded to 1.4.66. The difference between the two is 9 years, which is surprisingly large. This irresponsible behavior puts the network and data security of the majority of server users at great risk. > >4. Hidden backdoors endanger network and information security > >The autonomous running subsystem ME (Management Engine) developed by Intel has been embedded in almost all Intel CPUs since 2008. It is part of its vigorously promoted AMT (Active Management Technology), allowing system administrators to perform tasks remotely. As long as this function is activated, the computer can be accessed remotely regardless of whether the operating system is installed. Based on the redirection technology of peripherals such as optical drives, floppy drives, and USB, it can achieve the effect of physical contact with the user's computer. Hardware security expert Damien Zammit pointed out that ME is a backdoor that can fully access the memory, bypass the operating system firewall, send and receive network packets without the operating system user's knowledge, and users cannot disable ME. Intel AMT (Active Management Technology) based on ME technology was exposed to have a high-risk vulnerability (CVE-2017-5689) in 2017. Attackers can bypass the authentication mechanism and log in to the system directly to obtain the highest authority by setting the response field in the login parameters to empty. > >In August 2017, Russian security experts Mark Ermolov and Maxim Goryachy found a hidden switch suspected to be set by the NSA (National Security Agency) through reverse engineering technology. The switch is located in the HAP bit in the PCHSTERP0 field, but the flag bit is not recorded in the official document. Dramatically, HAP is the full name of High Assurance Platform, which belongs to the NSA-initiated project to build a next-generation security defense system. > >If the NSA directly shuts down the ME system by turning on the hidden switch of the HAP bit, and at the same time all other Intel CPUs in the world run the ME system by default, it is equivalent to the NSA being able to build an ideal monitoring environment where only it is protected and everyone else is "naked". This poses a great security threat to the critical information infrastructure of countries around the world, including China. At present, the software and hardware on the ME are closed source, and its security mainly relies on Intel's unilateral commitment, but the facts show that Intel's commitment is pale and unconvincing. Using Intel products poses serious risks to national security. > >5. It is recommended to initiate a cybersecurity review > >According to reports, nearly a quarter of Intel's global annual revenue of more than US$50 billion comes from the Chinese market. In 2021, Intel's CPU accounted for about 77% of the domestic desktop market and about 81% of the notebook market; in 2022, Intel's x86 server market share in China was about 91%. It can be said that Intel has made a lot of money in China, but the company has continued to do things that harm China's interests and threaten China's national security. > >Previously, the US government passed the so-called "Chips and Science Act" to unreasonably exclude and suppress China's semiconductor industry. Intel is the biggest beneficiary of this bill. Intel CEO Pat Gelsinger successfully tied Intel to the US government and became the largest partner of the US chip strategy. It not only received $8.5 billion in direct subsidies, but also $11 billion in low-interest loans. > >In order to please the US government, Intel actively took a stand to suppress China on the so-called Xinjiang-related issues, requiring its suppliers not to use any labor, purchase products or services from the Xinjiang region. In its financial report, it even listed Taiwan Province on a par with China, the United States, and Singapore, and took the initiative to cut off supply and service to Chinese companies such as Huawei and ZTE. This is a typical "holding the bowl to eat, and putting down the bowl to smash the pot". > >It is recommended to initiate a cybersecurity review of Intel's products sold in China to effectively safeguard China's national security and the legitimate rights and interests of Chinese consumers.
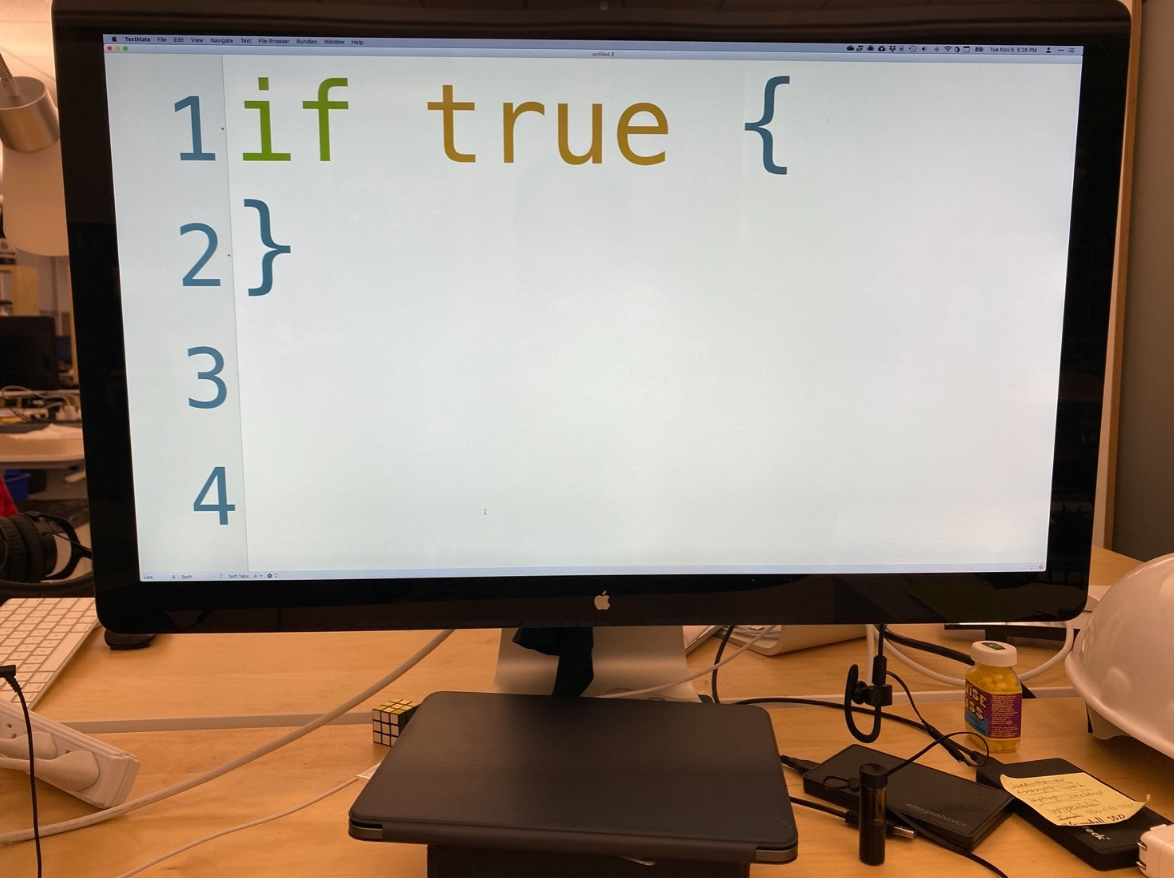
cross-posted from: https://lemmy.ml/post/21461907 > So, this uses a macro, but if you're thinking anything is possible with a macro, it's actually not in Rust. The input does still need to parse as valid Rust tokens. > > Which means the authors asked themselves at some point: Is the Rust syntax a superset of the Python syntax? > And well, it's not. In particular, some Python keywords will just be tokenized as an identifier (like a variable name). > > But it is close enough that the authors decided against requiring a massive string to be passed in, which does amuse me. 🙃
 cypherpunks
4d ago
•
100%
cypherpunks
4d ago
•
100%
::: spoiler i think the bottom text has it wrong.
this is probably a stronger argument to get people to vote for her:
 what she'll do
what she'll do
 what her opponent won't be able to do if she wins.
:::
what her opponent won't be able to do if she wins.
:::
 cypherpunks
1w ago
•
100%
cypherpunks
1w ago
•
100%
there are more photos here: https://commons.wikimedia.org/wiki/Category:Crown_shyness
it can be queried with this: https://util.unicode.org/UnicodeJsps/confusables.jsp
 cypherpunks
1w ago
•
100%
cypherpunks
1w ago
•
100%
headline was more exciting before i read the last four words of it
 cypherpunks
1w ago
•
97%
cypherpunks
1w ago
•
97%

 cypherpunks
1w ago
•
88%
cypherpunks
1w ago
•
88%
i can't help but wonder if there isn't some more useful science that these scientists could be doing (i write, while reading garbage on the internet)
 cypherpunks
2w ago
•
100%
cypherpunks
2w ago
•
100%
All two-letter TLDs are ccTLDs.
However, several of them are not in ISO 3166-1.
cross-posted from: https://lemmy.ml/post/21201228 > cross-posted from: https://lemmy.world/post/20643795 > > > It's early morning, and Zelda Montes walks briskly through the crisp New York air as they head to Google's headquarters on Manhattan’s 9th Avenue. Montes, who self-identifies as they, fumbles with their ID card at the entrance, blending in with the steady stream of Googlers swiping through the security barriers as if it were just another day at the office. > > > > Armed with an oversized tote bag, Montes pulls back their purple hair and heads to the 13th-floor canteen to order their usual: a dirty chai and an egg, avocado, and cheese sandwich with a bowl of raspberries. > > > > Their hands tremble slightly as they grip the coffee cup. > > > > Locking eyes with two others, they get the signal that the coast is clear, head down to the entrance, and sit. **The three Googlers unfurl their banners and begin chanting to demand that Google do one thing: Drop Project Nimbus.** > > > > But this will be the last time they sit inside Google's New York office as Googlers, as Google itself refers to its own employees. "Getting fired felt like a possibility but never a reality," remarked Montes, one of 50 employees fired by Google for staging a 10-hour sit-in at one of its American offices in April. > > > > For the last three years, Montes has been one of several activists calling for Google to drop Project Nimbus, a partnership Google and Amazon have with the Israeli government reportedly worth $1.2bn.
cross-posted from: https://lemmy.world/post/20643795 > It's early morning, and Zelda Montes walks briskly through the crisp New York air as they head to Google's headquarters on Manhattan’s 9th Avenue. Montes, who self-identifies as they, fumbles with their ID card at the entrance, blending in with the steady stream of Googlers swiping through the security barriers as if it were just another day at the office. > > Armed with an oversized tote bag, Montes pulls back their purple hair and heads to the 13th-floor canteen to order their usual: a dirty chai and an egg, avocado, and cheese sandwich with a bowl of raspberries. > > Their hands tremble slightly as they grip the coffee cup. > > Locking eyes with two others, they get the signal that the coast is clear, head down to the entrance, and sit. **The three Googlers unfurl their banners and begin chanting to demand that Google do one thing: Drop Project Nimbus.** > > But this will be the last time they sit inside Google's New York office as Googlers, as Google itself refers to its own employees. "Getting fired felt like a possibility but never a reality," remarked Montes, one of 50 employees fired by Google for staging a 10-hour sit-in at one of its American offices in April. > > For the last three years, Montes has been one of several activists calling for Google to drop Project Nimbus, a partnership Google and Amazon have with the Israeli government reportedly worth $1.2bn.
 www.theverge.com
www.theverge.com
 cypherpunks
2w ago
•
100%
cypherpunks
2w ago
•
100%
I don’t think any of his stuff would seem shocking by today’s standards.
 cypherpunks
2w ago
•
100%
cypherpunks
2w ago
•
100%
Or you could just… learn to use the modern internet that 60% of internet traffic uses? Not everyone has a dedicated IPv4 anymore, we are in the days of mobile networks and CGNAT. IPv4 exhaustion is here today.
Where are you getting 60%? Google's IPv6 Adoption page has it under 50% still:
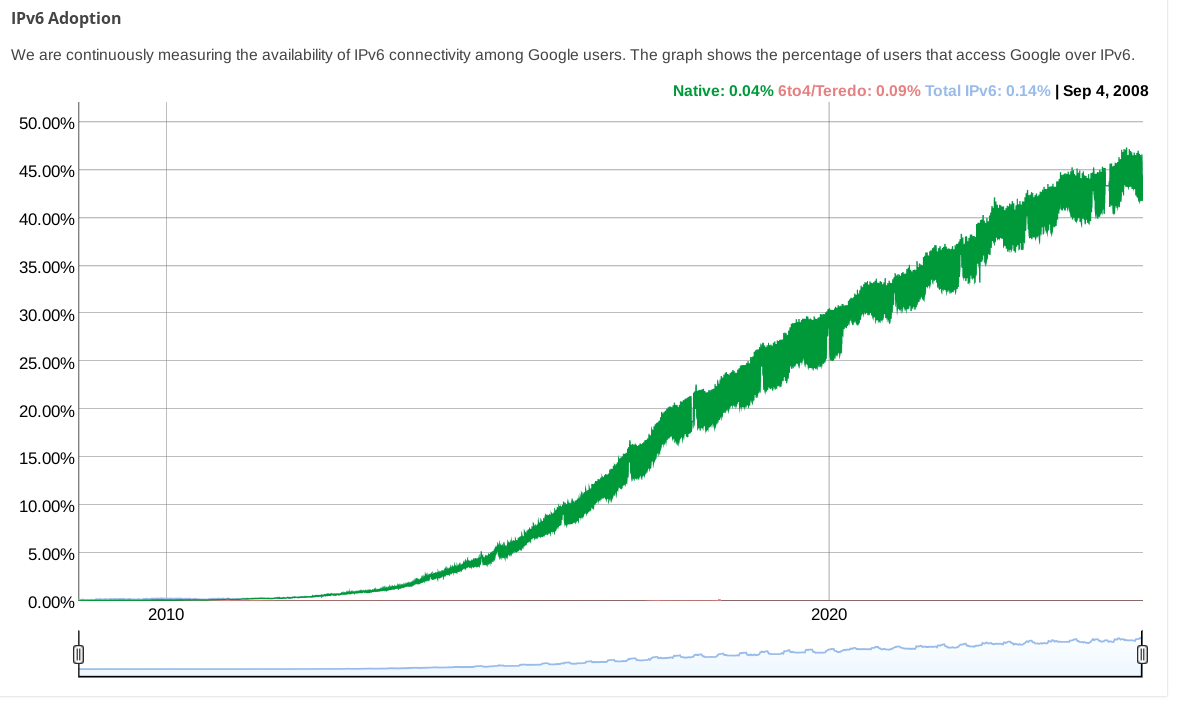
(while other stats pages from big CDNs show even less)
 cypherpunks
2w ago
•
100%
cypherpunks
2w ago
•
100%
Sounds good, until looking closer and finding out: "For an initial period of 99 years, the United Kingdom will be authorised to exercise with respect to Diego Garcia the sovereign rights and authorities of Mauritius required to ensure the continued operation of the base well into the next century" 😦
 cypherpunks
2w ago
•
100%
cypherpunks
2w ago
•
100%
If you have ::/0 in your AllowedIPs and v6 connections are bypassing your VPN, that is strange.
What does ip route get 2a00:1450:400f:801::200e (an IPv6 address for google) say?
I haven't used wireguard with NetworkManager, but using wg-quick it certainly adds a default v6 route when you have ::/0 in AllowedIPs.
 cypherpunks
2w ago
•
100%
cypherpunks
2w ago
•
100%
You could edit your configuration to change the wireguard connection's AllowedIPs from 0.0.0.0/0 to 0.0.0.0/0,::/0 so that IPv6 traffic is routed over it. Regardless of if your wireguard endpoint actually supports it, this will at least stop IPv6 traffic from leaking.
 cypherpunks
2w ago
•
100%
cypherpunks
2w ago
•
100%
ipv4 with an extra octet
that was proposed as "IPv4.1" on April 1, 2011: https://web.archive.org/web/20110404094446/http://packetlife.net/blog/2011/apr/1/alternative-ipv6-works/
 cypherpunks
2w ago
•
85%
cypherpunks
2w ago
•
85%
The article text doesn't support the headline ("Biden helped end the dockers strike by saying reopening the ports to help Hurricane Helene victims would be patriotic"):
“ With the grace of God, and the goodwill of neighbors, it’s gonna hold,” President Joe Biden told reporters Thursday night after the agreement.
In a statement later, Biden applauded both sides “for acting patriotically to reopen our ports and ensure the availability of critical supplies for Hurricane Helene recovery and rebuilding.”
[...]
Thursday’s deal came after Biden administration officials met with foreign-owned shipping companies before dawn on Zoom, according to a person briefed on the day’s events who asked not to be identified because the talks were private. The White House wanted to increase pressure to settle, emphasizing the responsibility to reopen the ports to help with recovery from Hurricane Helene, the person said.
Acting Labor Secretary Julie Su told them she could get the union to the bargaining table to extend the contract if the carriers made a higher wage offer. Chief of Staff Jeff Zients told the carriers they had to make an offer by the end of the day so a manmade strike wouldn’t worsen a natural disaster, the person said.
By midday the Maritime Alliance members agreed to a large increase, bringing about the agreement, according to the person.
 gizmodo.com
gizmodo.com
cross-posted from: https://hexbear.net/post/3613920 > https://archive.ph/tR7s6 > > Get fuuuuuuuuuuuuuucked > > “This isn’t going to stop,” Allen told the New York Times. “Art is dead, dude. It’s over. A.I. won. Humans lost.” > > "But I still want to get paid for it."
 cypherpunks
2w ago
•
100%
cypherpunks
2w ago
•
100%
In some places it is:

 cypherpunks
2w ago
•
85%
cypherpunks
2w ago
•
85%
would this text land differently if "public school" were replaced with "school"? 🤔
 cypherpunks
2w ago
•
100%
cypherpunks
2w ago
•
100%
see it's conciser?